Forcing SSL for Requests to MMDB
This article explains how to require SSL encryption for incoming connections to your MetaMiner Database (MMDB) and other databases and deny un-encrypted connections.
On PostgreSQL server for Linux/UNIX OS, follow these steps to require SSL encryption for all connections:
- Open the pg_hba.conf configuration file for editing.
-
Add the following rules:
# Allow local connections through Unix domain sockets: local all all peer # Allow non-encrypted local TCP connections with passwords: host all all 127.0.0.1/32 md5 host all all ::1/128 md5 # Reject any other non-encrypted TCP connection: hostnossl all all 0.0.0.0/0 reject hostnossl all all ::/0 reject
On PostgreSQL server for Windows OS, the incoming requests from external networks are authenticated and allowed access to MMDB by ODBC/JDBC.
To configure your ODBC driver that SSL is required:
-
Ensure SSL is enabled on MMDB.
-
Log in to PostgreSQL server host where your MMDB is stored.
-
Open the ODBC 64-bit connection to MMDB.
The ODBC dialog window opens:
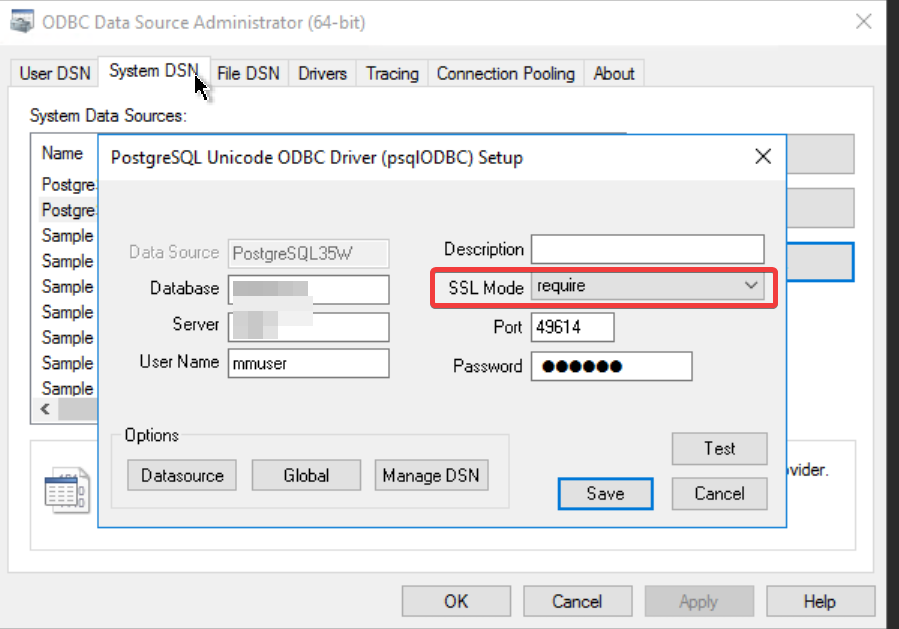
-
Change the SSL Mode to Require.
There are five different SSL modes available. Select the appropriate one as per your SSL set up on the database.
-
Click Test and check the results.
-
On success, click Save.
Note
PostgreSQL database with SSL enabled but SSL Mode not required will accept both SSL & Non SSL connection requests.